Welcome again in one of the lessons of learning hacker mobile. Today will be an important lesson. Through this article, you will be able to learn about many things about hackers and the hacking process.
For the beginner hacker, he must first focus on the following questions:
What is the process of hacking and espionage?
A hack is an attempt by a person to obtain unauthorized information from your computer. That is, he can access your device and view the content in it [pictures - files - videos…] also when information and data are changed or taken from your device without your permission. The hacker can perform many tasks from your computer, for example viewing the desktop of your device or opening the mobile camera or computer. See photos and videos on your device. The hacker can also save and add files to your computer.
A simple example of what a hacker can see on your computer.
Spy on your desktop and watch what you do live broadcasts
Open your mobile camera or computer and watch you live
Who are the hackers?
There are many types of hacker and the most famous of them are black hacker, white hacker, and gray hacker.
- Black hacker: Its goal is to destroy devices, spy on people, steal data, destroy websites, hack banks.
- White hacker: Its goal is to check websites and report vulnerabilities, fix what has been sabotaged by the black hacker, help people understand the breach, develop protection at sites and banks.
- Gray hacker: his goal is money only, if he breaks into a site, he sees what is appropriate for him and is considered among the smartest hackers, because he can take advantage of the advantages of black and white hackers at the same time.
There are other types that you can find through the topic " Types of hackers "
What are the things that help hackers to penetrate your device?
1- The presence of a patch or Trojan file on your device
A regular hacker cannot access your computer unless there is a patch or Trojan on your computer. These files are considered the gateway to your computer, and a regular hacker can deceive you by sending this patch or Trojan to you, and as soon as you accept it and download and open it on your computer, you have given all the powers to the hacker to enter your computer. The patch can be in the form of an image, file, video, the patch is integrated with the file sent to you and you will not be able to detect the file in case you do not have a strong antivirus. Even in some cases, when a professional hacker can create an encrypted Trojan, it is not detected by the protection programs.
2- Your device is connected to the Internet
The normal hacker cannot penetrate in the event that your device is not connected to the Internet, in case you feel that your device is hacked, all you have to do is disconnect the Internet cable, and the connection between you and your device will be blocked. In other cases, the advanced hacker can penetrate your device via wireless or by connecting to the bluetooth, and in rare cases via radio waves, he can execute some commands on your device. In very rare cases, these methods are used by governments. They can program harmful viruses. These viruses can spread automatically between devices and USB keys, and it is difficult to detect them. These viruses can execute many commands without the need for the Internet.
3- Spyware
In order for a regular hacker to penetrate your computer, it must have programs that enable it to create patches and Trojans in order to send them to you, and there are many famous programs known to be used in the field of penetration, some other programs are only used by their owners, and the Kali Linux system is basically the most powerful penetration system currently Only the elite in the field of penetration can use it in hacking operations. As for the average hacker, he can use some programs that make it easier for him to control the hacker's devices. We have explained one of these programs in a previous topic under the title " Najrat "
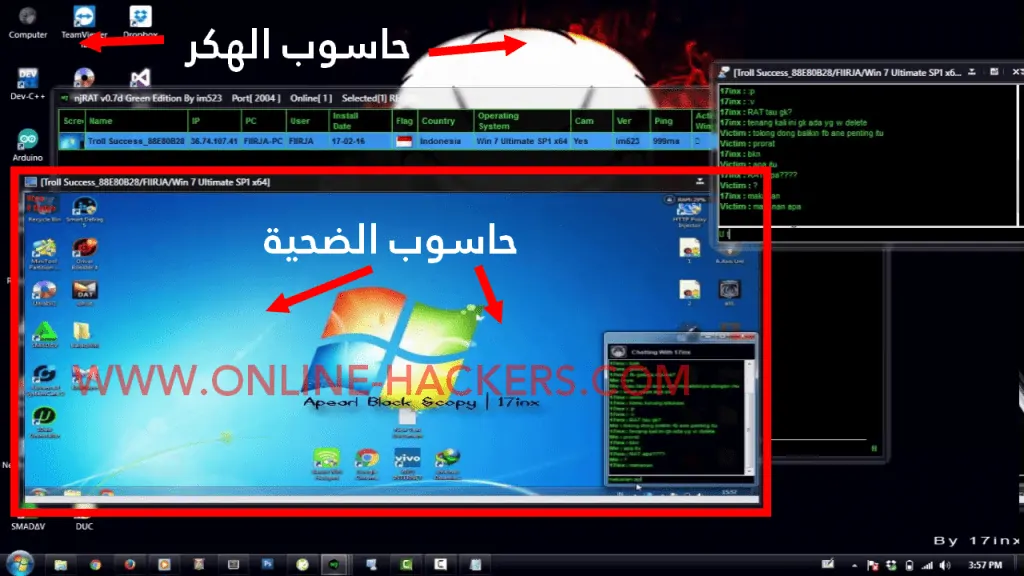
How can a hacker access to your computer ?
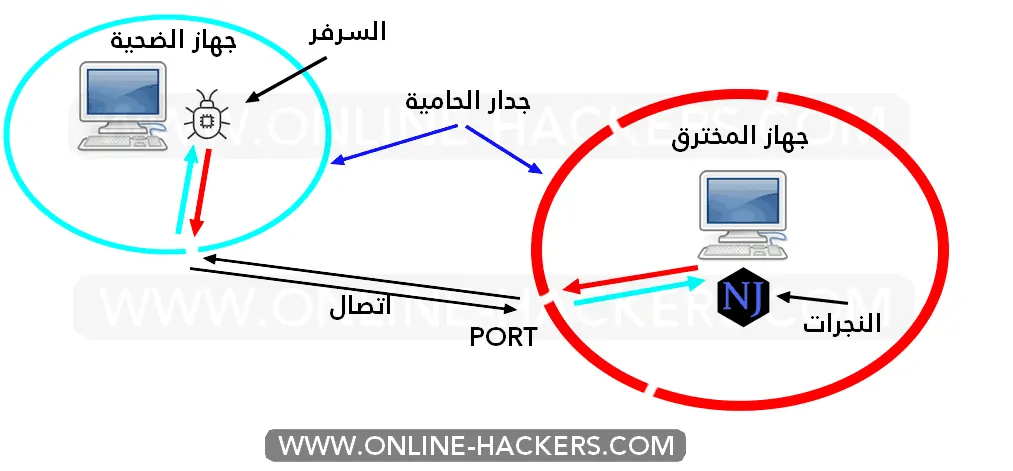
As I said in the past, a regular hacker cannot penetrate your computer directly, there must first be a patch or Trojan in your computer activated. There are many methods that a hacker can use to trap you, for example by sending the Trojan file in the form of an image or in the form of a video. In the case of random penetration, some hackers merge the patch with the program’s activation files and upload them to the sites. Anyone who downloads the software will hack your device and leak all the information from your device. In the above image, we have explained how the hacker can communicate via "server = patch = Trojan". When the victim opens the file sent to him by the hacker, he opens the “port” port, which is a gateway to the device. Without it, the hacker will not be able to connect to your device.
How can the hacker access a particular computer?
Ordinary hackers cannot penetrate your device without the patch file that we talked about, we are talking about hacking your device, and we have found many conditions that must be met in your device and in the hacker in order for the process of hacking your device to take place.
1- The victim’s device must have the patch file, and the communication port must be open in the victim’s device.
2- The hacker must know the victim's IP, and also know the existence of a vulnerability or port in the devices and the programs in the victim's device.
3- It is impossible for a regular hacker to penetrate your device in the absence of the first and second conditions, in addition to the case that the victim’s device has a protection program also, it will be difficult to penetrate the victim’s device because the protection program may disable or expose everything that the hacker does.
There are few cases when the hacker is very professional, he can find gaps in one of the programs or systems, for example, the old systems Windows XP had many security holes, in the case the hacker was a professional he could only by knowing your IP and through the vulnerability in the system To infiltrate your device and penetrate you without the patch file. The reason is that prior knowledge of the existence of a vulnerability in your system, the hacker may dispense with sending a patch to you.
What is the IP number I study?
It is the address of each user of the Internet, that is, it is the number that identifies the location of the computer while browsing the Internet. It consists of 4 numbers, and each part of them refers to a specific address.
The IP number is variable and is not fixed, as it changes with each entry to the Internet .. In other words, suppose you connect to the Internet and look at your IP number and find that:
If you watch the video, you may understand what the IP means if you do not watch the video. In short, the IP is The device address consists of 4 digits. Every device connected to the Internet will have a different IP address, and each number forms an address and consists of the following.
Your country number - the address of the Internet company - the organization you use - the address of the user
It is only through your IP that you can know your country, the operator you are using, and your device exactly. I mean, in the event that you entered the deep web, for example, the police can through your IP to know your location and contact the communication company and determine your identity, and you will be arrested quickly. And a person can change his IP by changing the place of communication and the company of communication and by changing the location of the country. For example, if your current IP is 212.123.123.200, and you closed the connection and called from GED, the IP will be changed to 212.123.123.366. Note that the change occurred only in the last two numbers, and it constitutes the number of those connected to the network. For example, if your home Wi-Fi is connected to 5 people, their IP addresses will be as follows
212.123.123.1
212.123.123.2
212.123.123.3
212.123.123.4
212.123.123.5
A novice hacker may face many problems when hacking a person’s device who changes its location always, when it takes the hacker to install the patch on the victim’s device, even if the IP is changed, the patch will send the new IP to the hacker automatically.
How does your computer get infected with the batch file, Trojan, or even viruses?
1- Sending the patch program to you
As I said in the past, the hacker can send the patch to you in the form of a picture, video, file, program, either via chat, or upload it in a USB or CD file, or often the hacker lures you with something you want in order to download what it sends to you, for example telling you, download Hacker games program, PUBG hacker program, hacker program Clash of Clans, a program that increases jewelry in a game.
2- Via spam in the e-mail
The hacker can penetrate websites, pull mailing lists and use them in the process of sending Trojans in messages. For example, you may find your Gmail account with a list of " spam messages ". These messages are sent in huge numbers that may reach a million messages to random people. If you open the patch, it will be done. Hacking you and pulling all data from your device in addition to spying on you
3- Downloading files and programs from unreliable sites
The average person always downloads programs and files from unreliable and suspicious sites, for example, by batch activating a specific program that may be combined with a spyware program, and torrent files are often bombed with spyware because they have less protection and their sites do not check files.
4- Entering suspicious websites
Many of the suspicious sites that do not contain the green shield or green lock symbol next to their site may have malware that is automatically downloaded to your computer without you noticing, and you should not enter them, for example, porn sites, sites that do not start with https. For example, our website online-hackers.com you will find the green lock icon next to our site, which indicates that our site is reliable and offers 100% safe programs, but if our site is not available on https, you must close the site and do not download any program from it.
How does the hacker choose the device that he wants to hack?
As I said in the previous two types of penetration would like. Targeted hacking, for example when you want to hack a specific person and want to access your device. And the random, non-targeted penetration, for example, penetration of the largest number of victims and the use of their devices to penetrate the site, for example.
Random penetration, as I said, when a person's device has a program or system with a specific vulnerability, for example:
In 2015, a serious security flaw was discovered in Microsoft's operating systems that enables anyone to exploit this vulnerability to penetrate the largest number of devices.
For example, I want to hack devices connected to the university's Wi-Fi 😉 I will enter the Router by hacking the Wi-Fi network. I am checking all IPs connected to the Rotor. For example, I will set the goal to check the following IPs.
From 212.123.123.1 to 212.123.123.999
It will be checked all the devices , which number 999 device in the case of finding a device that the port will be open and will let me know that I could penetrate the device with ease. I explained in a previous topic how the process of hacking devices is done through the IP only and connecting to the Wi-Fi network. “ Hacking a cell phone through an IP. ”
What's the famous program to the hakars ?
Most of the programs that are used in the hacking are programmed by hackers who are reputable in their field. A hacker is always proficient in programming and all kinds of programming. Advanced hackers use systems such as the "Kali Linux system", the old "backtrack" system, and others ... which are specialized in examining security vulnerabilities. And through it, programs are programmed to help Alhakz hack operations without using programming. I explained an example of one of the programs that the hacker uses in hacking operations and the name of the program was " Najrat "
How do you know if your device is hacked or not?
When you reach an advanced stage of your understanding of the field of information security, you may discover whether the device is hacked or not without the need for protection software. There are many things that may be a sign of a hacker in your device, whether a computer or a phone, including the following:
1- The Internet is slow: There is a high possibility that your internet is slow due to the presence of a hacker in your computer, and the reason for the weight of the internet is often because the hacker uses your internet to upload a file from your computer to his computer and causes you to have a heavy internet. Another possibility is that the hacker is using your computer in the "zombie attack" that we talked about earlier. Also, when the hacker is running the device's camera, this causes a heavy load on the Internet, because it displays a live video from your device, which may cause you to become heavy and lash in the device.
2- The presence of new files on your computer: If you carefully observe, you may discover that some files have been erased or moved from one place to another, and this is evidence that someone is manipulating your files.
3- Random pages pop up: When you find many pages from your computer for sites that you have not visited before, this may be evidence that a hacker has installed an ad program in your computer. The goal of these programs is to open random windows on your computer aimed at profit from offers CPA.
4- Download the Trojant Protection Program: There are many programs that protect you from hacking, and I have tried almost all known protection devices and I do not recommend them. Why ? Because when hackers develop a new virus or Trojan, the first thing to do is to encrypt the virus so that it is not detected by known programs. I am talking about a program such as “Avast” “Casper Ski” and other known programs. If you want to know the programs that I use in the process of protecting my devices, I recommend Malwarebyte and Zemana
5- Manual detection: You can manually detect the presence of any spyware on your computer by following the following steps. From the keypad we press the Windows sign with the R button

1- A CMD page will pop up for you, typing msconfig
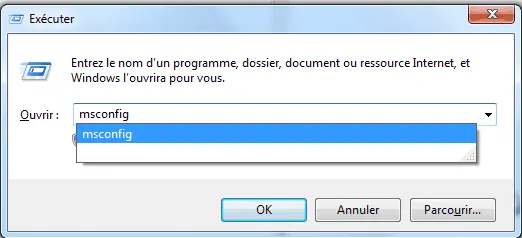
2- A page will appear for you with many options. We choose the option shown in the image
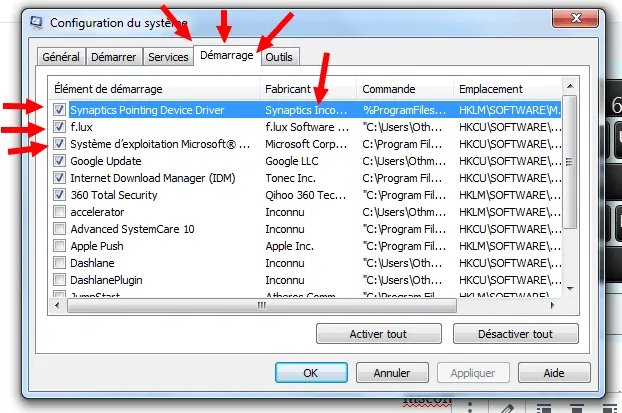
4- You will find all the programs that run with the operation of your computer. If you find any program that you have not downloaded before, know that it is a Trojan.
What are the most important precautions to be taken to protect against hackers?
1- Do not enter suspicious sites such as sites that contain pornographic movies and pictures because hackers use such sites to enter spyware files to victims, where the spyware (patch) file is installed automatically on the device as soon as the person enters the site !!
2- Not to receive any files during (chat) from untrusted people, especially if these files have an extension (exe) such as (love.exe) or if they are files with two extensions such as (ahmed.pif.jpg) and such files are They are programs that plant spyware files in your computer, so hackers can enter your computer and cause you harm and problems ..
3- Always try to change the password periodically, as it is vulnerable to penetration. Each account has a different password.
4- Do not receive any file and download it to the hard disk of your personal computer if you are not sure of its source.
5- Use the latest protection programs from hackers and viruses and make a periodic and comprehensive scan on your device in close periods, especially if you can use the Internet on a daily basis ..
6- Put secret numbers on your important files where only those who know the password can open them, which is you .
7- Make sure to raise the Internet connection cable after using the Internet.
8- Not to open any email from an unknown source because hackers use e-mail messages to send spyware files to victims.
9- Not to keep any personal information inside your device, such as private messages, photos, or important files, and other bank information such as account numbers or fake , charged visa numbers ..
What are the most important things that hackers are looking for?
We learned in the past about “ types of hackers ” and that every hacker has a goal of penetrating devices, whether targeted or random, some penetrate the source of fun only, others for espionage. There are many reasons, and we mention the following.
1- Fun: a novice hacker enjoys penetrating people for fun only, while he penetrates his friends and one of his family members in order to spy on them. And to be honest with you, I too, in my early years of 2011, I used to penetrate my friends just for fun and I did not harm anyone.
2- Self-restraint: When the hacker is between the age of 14-18, he often learns to penetrate only in order to prove himself in this field to find himself able to penetrate people using programs, he was told about his capabilities in the field of penetration.
3- Spying on people: Spying on people is a strong motive that makes hackers have the desire to have more victims. They use a variety of methods to obtain cutter victims.
4- Blackmail: When the black hacker learns methods of penetration, he uses them in espionage operations, filming videos, or leaking clips from a computer or phone, it is used to blackmail a person in order to obtain important sums of money.
5- Stealing accounts: Once hacked into your device, the hacker can get all your Facebook accounts. With the click of a button, it will launch the Keylogger program, which records all passwords for the accounts on the computer.
6- Exploiting a device for profit: In the year 2019, a new method appeared in the exploitation of victims' devices, so that it became possible to penetrate people's devices and use them in the Bitcoin mining process, a single hacker can mine more than 20 bitcoins per day only from his victims.
7- Using your device as a weapon: I talked about a previous topic how a hacker can make your device a deadly weapon against websites, once the hacker breaks into your device, your device will become a zombie soldier at the hacker and he will use it in attacks on devices.
What is the most popular spyware detection method?
There are many ways that a person can find out if your computer has a Trojan or spyware patch, and I have explained some methods above. There are other methods, but I will not address them in this matter because of the many methods. But I will introduce you to some programs that will scan your device completely and wipe all Trojans from your device.
The first method: Spyware and virus detection software
We will use in this explanation the program that we talked about a little while ago.
1- We download the protection program: Zemana [official website: www.zemana.com]
2- After downloading the program, we download it to the device and install it.
3- We open it and perform a SCAN operation for the device
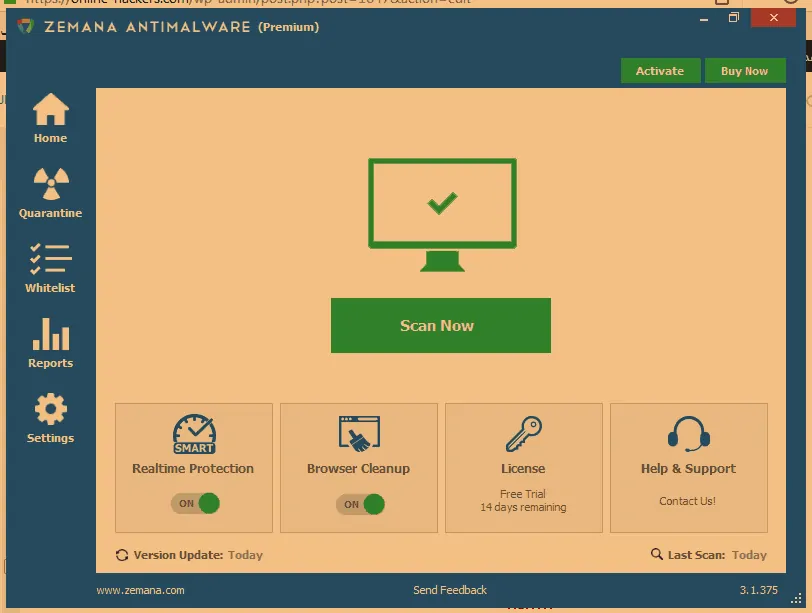
4- The program is experimental for 15 days when I searched for a serial for it to activate it for life for free 😉
5- After the program finishes the scanning process, if you find any name for the viruses discovered in this way. horse trojan so know that your computer was hacked Delete the files from your device and restart the device.
The second program is Malwarebyte
1- We download the program from the following link Malwarebyte or from the official website [malwarebytes.com]
2- After downloading and installing it on your device
3- Open the device and perform the scan for your device, the scanning process will take minutes.
4- After completing the examination, apply the same steps. And I searched for surreal as well
You can use the two programs to protect your device, but in the event that your device is weak and cannot tolerate protection software, you can use only one and I recommend that you use malwarebytes
Method 2: Using the Registry
Click on the Start button.
- Write in the Run field the command: rigedit
- Open the following folders according to the order in the Registery Editor list:
- HKEY_LOCAL_MACHINE
- Software
- Microsoft
- Windows
- Current Version
- Run
- Now from the Registry Editor window, look to the right of the window in the split screen, you will see under the menu Names The names of the files that work with the startup menu and their matches in the Data list are file titles.
Note the files carefully, and if you find a file that does not meet an address in the data, or it appears in front of a small arrow <- it is a spy file as it does not have a specific address in Windows.
Get rid of it by pressing the right mouse button, then Delete
Method 3: With the command: msconfig

1- Type in the Run box the following command: msconfig
2- A System Configuration Utility window will appear
3- Select from this window from the top of the Start up section

4- The screen displays the programs that start working directly with the start of the device.
5- Check these programs well by looking. If you suspect that there are strange programs that you did not install on your device, cancel their operation and try to determine the path of the program and wipe it from your computer.
